Ingress Controller V2 TargetGroupBinding使用方法 场景
实现EC2到EKS的平滑过渡,想在暴露EKS Ingress的时候使用原来给EC2使用的ALB,因此可以使用Ingress Controller V2版本的TargetGroupBinding新功能。
Demo步骤
- 安装ALBIngressControllerv2版本, 或将v1版本迁移至v2
- 创建一个新的targetgroup,并记录下arn,后续要把该arn写到TargetGroupBinding的CR当中
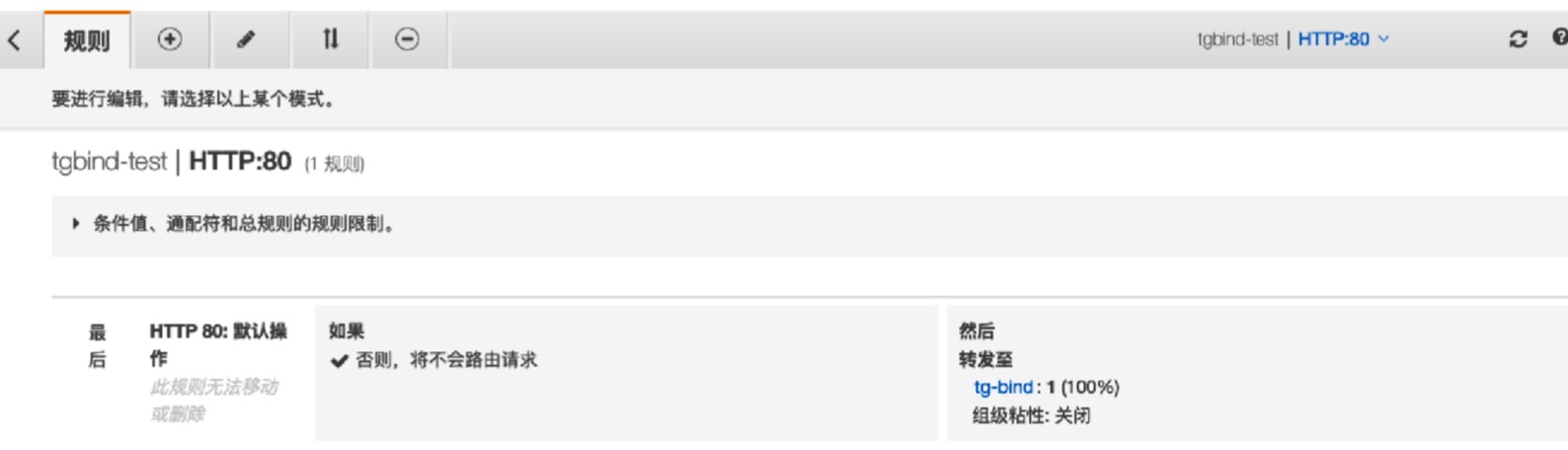
- 在alb上配置到目标组的路由策略
- 赋予nodegroup上的iam role能够注册到目标组的权限
- 创建ns/deployment/services
1 | apiVersion: apps/v1 |
- service暴露完成之后,不再需要创建ingress了,直接和targetgroup进行绑定,(kubectl logs aws-load-balancer-controller-xxx -f -n kube-system可查看是否发生错误),注册到目标组的方式通过targetType来指定,支持ip与instance两种方式,绑定后,实例或ip会自动注册到目标组中
-
apiVersion: elbv2.k8s.aws/v1alpha1 kind: TargetGroupBinding metadata: name: wormhole-tg-bind spec: targetType: instance serviceRef: name: wormhole-svc port: 80 targetGroupArn: arn:aws:elasticloadbalancer:xxxxxx:xxxxxxxx:targetgroup/tg-bind 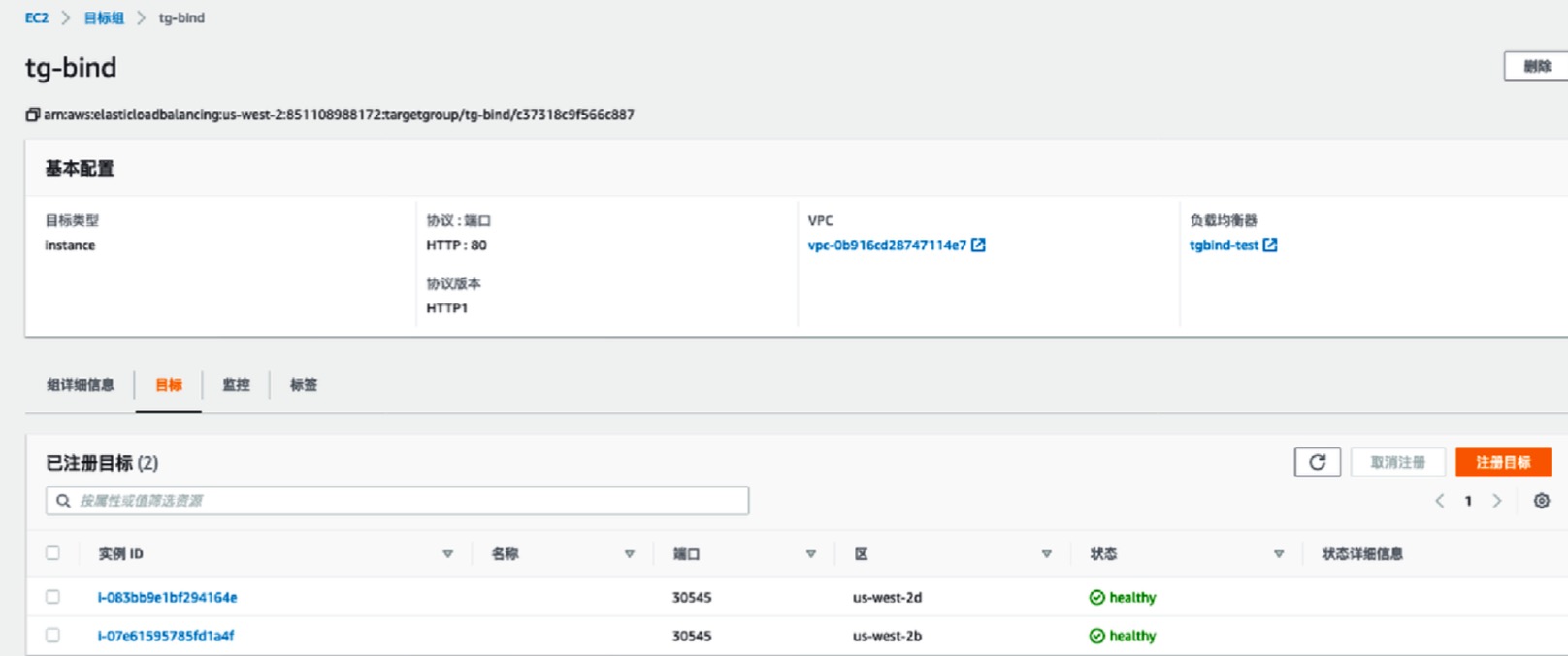
-
注意
- 和一般的ingress不同,路由策略要在alb侦听器上自行编辑
- 实例端口也不会自动在安全组中开放,需要在node使用的安全组上自行打开
- node需要有足够的权限注册到目标组中